This post originally appeared on the Gartner Blog Network.
If you use public cloud services at some scale, then you know you must tag your resources. You know you must use tagging so that your cost reports get nicely broken down; so that you can create resource groups to enable inventory, governance, automation and access control. You know this but, still, you are not doing it. Or maybe you think you are, but only less than half of your cloud resources are tagged in the way you want.
Unfortunately, this situation is something I hear in my inquiry calls more often than not. Why? Is it because of lack of enforcement measures? Is it because your cloud consumers are not disciplined? Or because tags are perceived just as administrative burden? The answer is all of the above. Tagging is a complex matter and some people assume that distributing a list of “mandatory” tags is enough. But that’s only the very beginning of your tagging strategy.
Common guidance on tagging usually stops at providing a list of suggested tags and describing the technical mechanisms for their implementation. While this is certainly important, such guidance often does not consider the organizational impact of metadata management in highly dynamic environments. Internal resistance within an organization is often the primary cause of the failure of tagging initiatives. That’s why I decided to publish a guidance framework for “Implementing a Tagging Strategy for Cloud IaaS and PaaS” (paywall). The framework is now available to Gartner for Technical Professionals subscribers and it is depicted in the figure below.
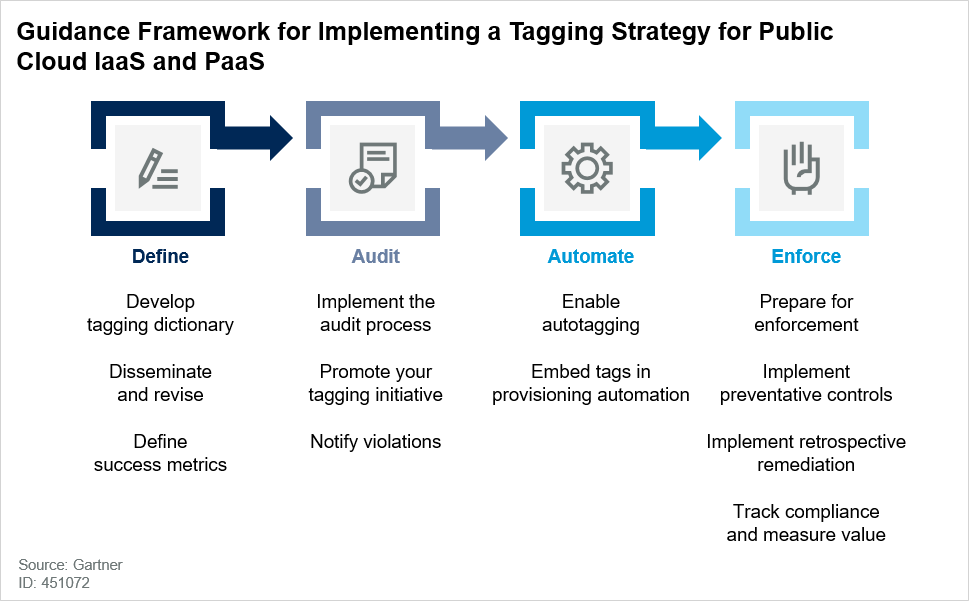
Defining your tagging dictionary is really just the beginning of your process, while enforcing tags is the very last step. The activities in between serve to internally promote the value of tagging and to lower the overhead for their implementation. Promoting tags requires the communication of their benefits and use cases. Implementing tags can be made easier through automation.
We developed this framework to make sure you’re successful in your tagging initiative. Cloud providers offer lots of native tools and constructs to manage your tags. However, tagging is not just a technical problem. By following the Gartner framework, you will also manage the organizational impact of tags, mitigate internal resistance and ease their implementation.
The Gartner framework is available today behind paywall with a 30+ page research note that explains its application in details. To know more about this research, you can also schedule an inquiry call with me (inquiry@gartner.com) or talk to your Gartner representative.
Lastly, feel free to follow me on Twitter (@meinardi) or connect with me on LinkedIn for further updates on my research. Looking forward to talking to you!