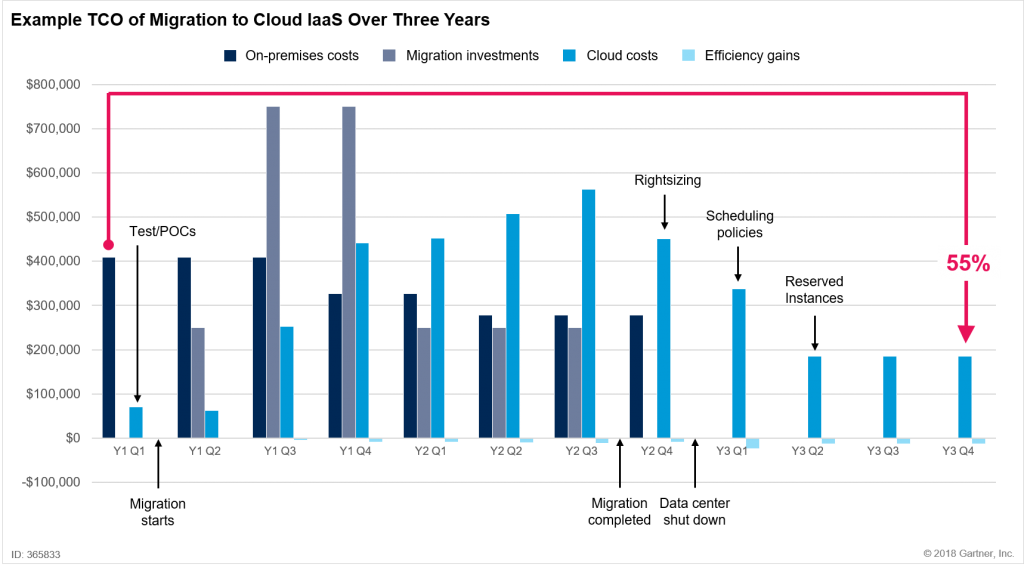
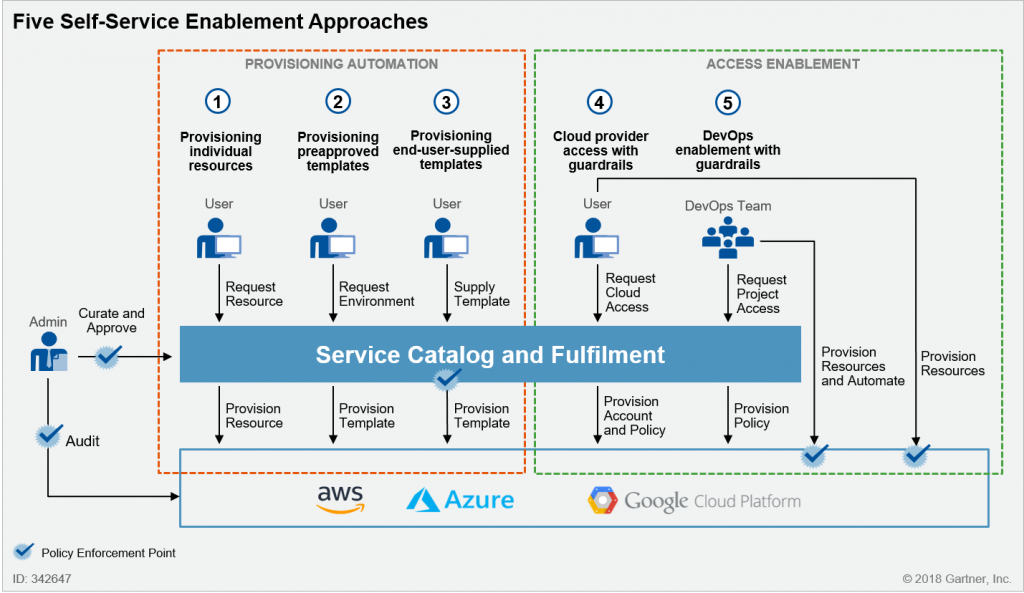
This post originally appeared on the Gartner Blog Network.
If you ever wondered what cloud management means and what it encompasses, Gartner has the answer. The newest cloud management framework has just been published as part of the research “Solution Criteria for Cloud Management Tools” (paywall).
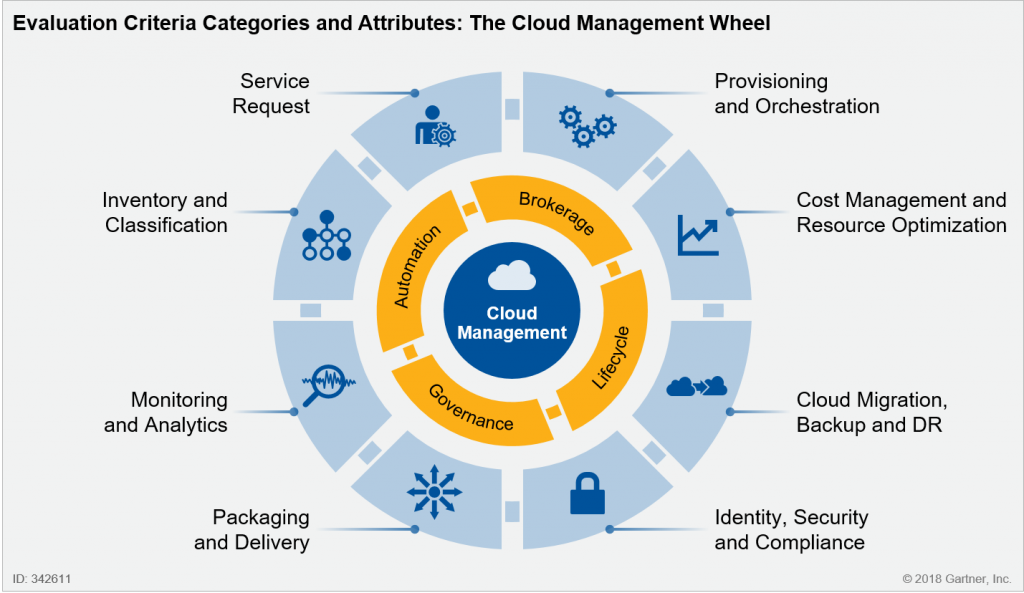
Cloud management is made of seven functional areas and five cross-functional attributes. The functional areas are specific to one use case, whereas the cross-functional attributes aim at broader goals that are common to multiple use cases. The outer ring of the “wheel” in the below figure below represents the functional areas, and the inner ring characterizes the cross-functional attributes.
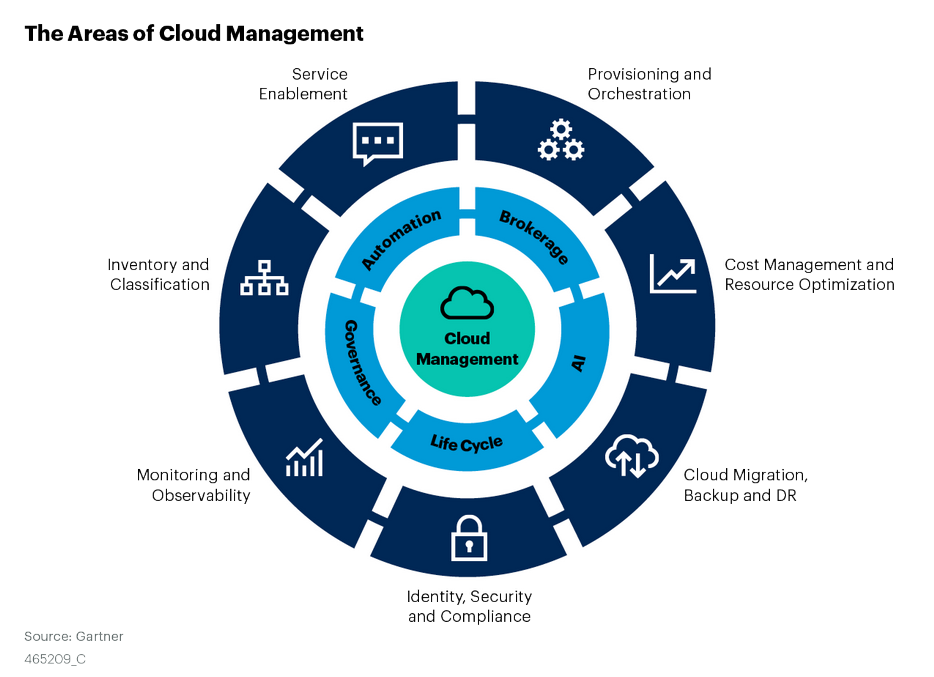
The research also “double clicks” on each category and provides a total of 201 capabilities that organizations should possess to manage public and private clouds. These capabilities are presented in form of requirements, which can be used to evaluate and select cloud management tools. The research comes in form of a toolkit that clients can download and customize to power their request-for-proposals (RFPs) efforts.
Major updates to the research include:
- Shift from platforms to tools: Although cloud management platforms (CMPs) are still out there, they’re no longer top of mind of clients according to our inquiries. In the last couple of years, we’ve observed the shift of the interest from broad general-purpose platforms to best-of-breed tools that have deeper functionality in a given area.
- Addition of observability criteria: These days, observability is certainly stealing the spotlight in the monitoring space. We added observability capabilities and adopted the term as part of the category name “Monitoring and Observability.”
- AI as cross-functional attribute: AI-powered analytics now touches several aspects of cloud management that we made it a cross-functional attribute (the middle ring of the wheel) in addition to the other four: automation, brokerage, governance and life cycle.
Often, organizations purchase a cloud management tool and implement their management strategy solely based on its available capabilities. With this research, we suggest the opposite approach. Define first what you need to manage and then select the tools that can provide you with the functionality you need.
You can access the full research at “Solution Criteria for Cloud Management Tools” (paywall). Should you want to discuss further, feel free to schedule an inquiry call with me by emailing inquiry@gartner.com or through your Gartner representative.
Follow me on Twitter (@meinardi) or connect with me on LinkedIn for further updates on my research. Looking forward to talking to you!